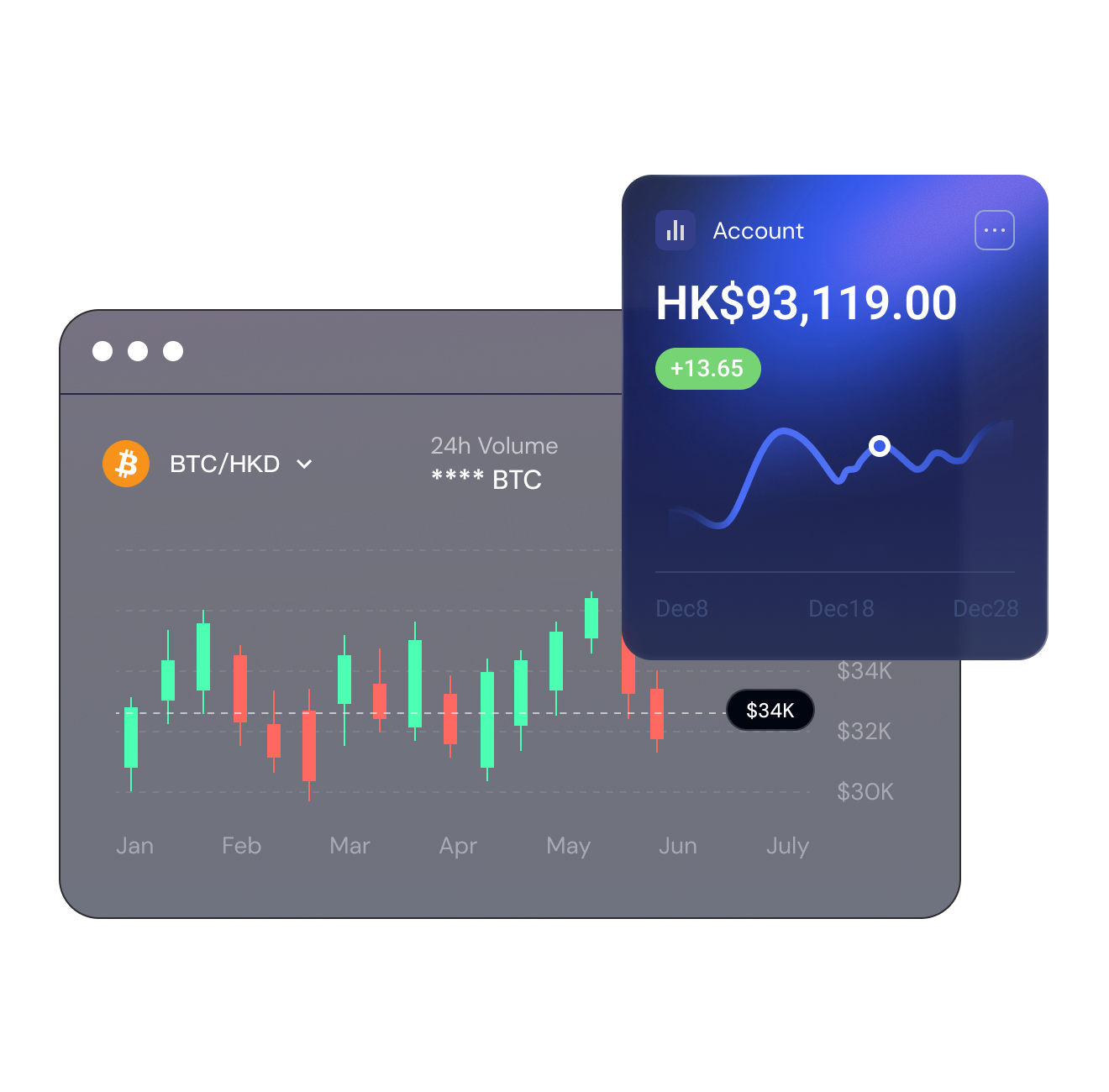
What is BitV?
BitV Exchange is committed to providing secure and compliant digital asset services for global users. We strictly adhere to Hong Kong regulatory requirements, employ a multi-layered risk control system, and comprehensively safeguard user asset security and transaction compliance. The platform supports mainstream cryptocurrency trading and is dedicated to building a transparent and trustworthy trading environment to promote the healthy development of the industry.